Leveraging ML/AI for Malware and Ransomware Detection
Safeguarding the Digital Frontier 🔐
In today’s interconnected digital landscape, the threats posed by malware and ransomware have become increasingly pervasive and sophisticated. Cybersecurity professionals face the daunting task of developing effective detection and mitigation strategies to safeguard sensitive data and critical systems. Fortunately, the rapid advancements in machine learning (ML) and artificial intelligence (AI) offer promising solutions to combat these threats. In this article, we will explore how ML and AI techniques are revolutionizing malware and ransomware detection, enhancing cybersecurity defenses for a safer digital future. We’ll also take a look at what the future holds for ML/AI in malware and ransomware detection.
The Traditional Approaches 🛶
Historically, signature-based detection and heuristic analysis have been the go-to methods for identifying known malware and ransomware variants. In the research paper by Rieck et al. (2011), the authors discuss the limitations of signature-based detection and heuristic analysis methods in identifying malware. While effective to some extent, these approaches struggle to keep pace with the ever-evolving threat landscape because they rely on predefined patterns or rules and struggle to keep pace with the rapidly evolving nature of malware [1]. Additionally, they often fail to detect zero-day attacks and lack the ability to identify emerging and polymorphic malware strains.
To overcome the limitations of traditional approaches, ML and AI algorithms have emerged as powerful tools in cybersecurity. These techniques enable computers to learn patterns, identify anomalies, and make informed decisions based on large-scale data analysis. ML models can be trained on vast datasets containing both benign and malicious samples to detect and classify malware and ransomware accurately [2]. The ability to learn from data and adapt to new threats makes ML and AI techniques a promising solution for malware and ransomware detection.
Let’s deal with malware first 🦠
ML algorithms can leverage features extracted from malware samples to build robust detection models. Feature engineering techniques, such as static analysis, dynamic analysis, and opcode analysis, provide valuable insights into the behavior and characteristics of malicious code. Supervised learning algorithms, including support vector machines (SVM) and random forests, can classify malware based on these features, achieving high detection accuracy.
An example of how ML is being used in malware detection:
ML models can learn patterns and features from a large dataset of known malware samples and benign files, enabling them to identify and classify potential malware instances.
For instance, a ML-based malware detection system may extract features such as file size, entropy, header information, API calls, opcode sequences, and other relevant attributes from executable files. These features serve as input to ML algorithms, such as support vector machines (SVM), random forests, or DNNs, which learn to distinguish between benign and malicious files based on the extracted features.
The ML model is trained on a diverse dataset of known malware and benign files, and during the detection phase, when encountering a new or unknown file, the ML model applies the learned knowledge to predict its likelihood of being malware.
The strength of machine learning in malware detection lies in its ability to generalize patterns and adapt to new and evolving threats. It can identify even previously unseen malware variants by recognizing similarities with known malicious patterns, enabling proactive defense against emerging threats [3].
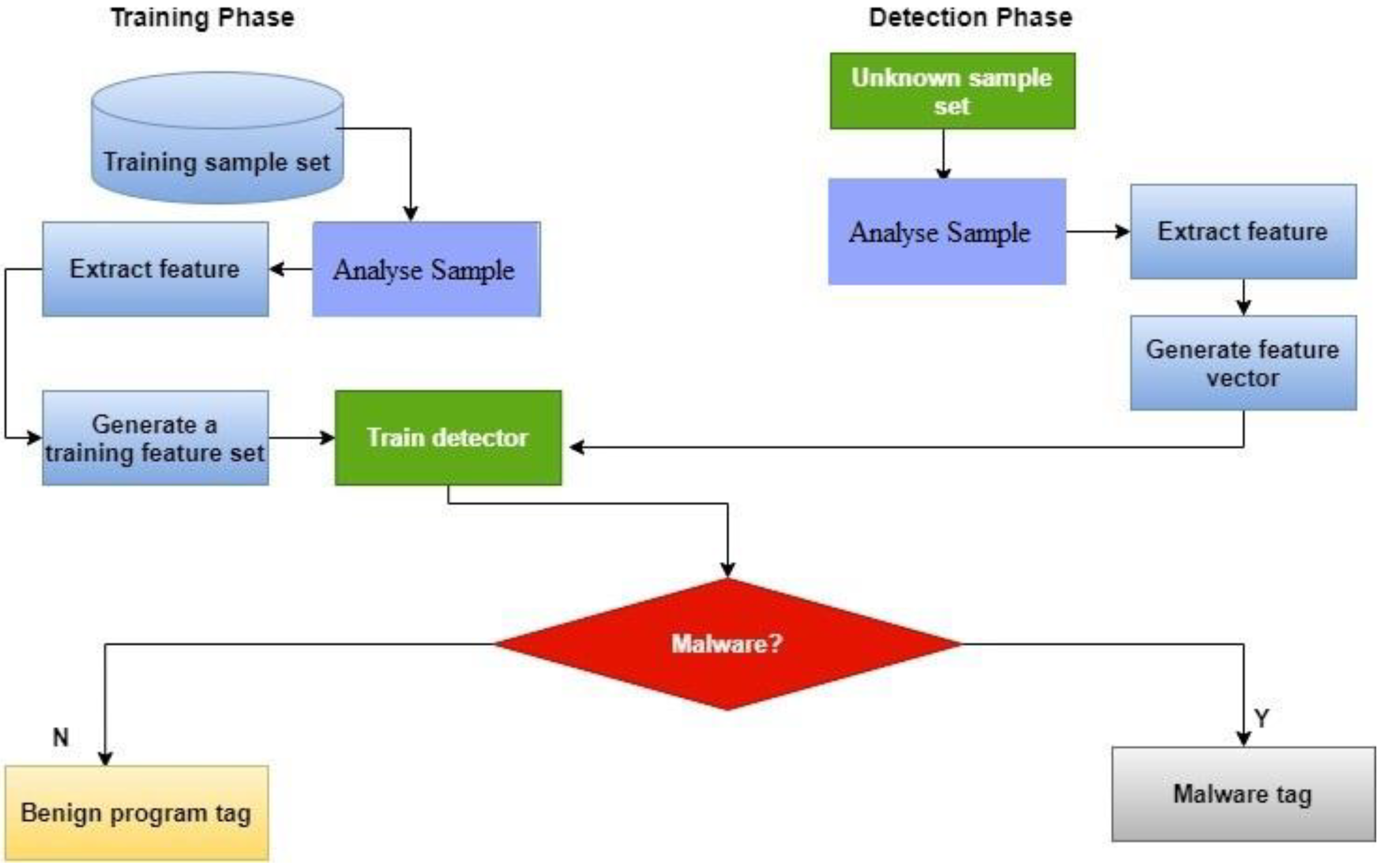
The following diagram illustrates the process of malware detection using ML algorithms
Research papers by Kolosnjaji et al. (2018) and Saxe and Berlin (2015) provide in-depth analysis and methodologies for malware detection using ML. The following diagram illustrates the process of malware detection using ML algorithms.
Now, let’s talk about ransomware 🗝️
Ransomware presents unique challenges due to its stealthy nature and evolving techniques. ML models can analyze patterns of behavior exhibited by ransomware samples to detect their presence. Behavioral analysis, combined with time-series analysis and anomaly detection, helps identify ransomware activities, such as file encryption and communication with command-and-control servers.
In a study by Poudyal et al. (2019), a multi-level ransomware detection framework utilizing natural language processing (NLP) and ML was proposed, demonstrating the effectiveness of the approach with a detection accuracy of 98.59%. The framework employed supervised ML algorithms and Apache Spark for efficient analysis of ransomware at different levels, leveraging techniques such as n-gram probabilities and TF-IDF.
WannaCry is one of the most well-known ransomware cyber-attacks which started spreading globally around May 2017. This attack used phishing emails to spread malicious software that encrypted certain files on the victim’s computer. The attackers then demanded payment in bitcoins in exchange for decrypting the files and allowing users to regain access to them. This cyber-attack affected an estimated 230,000 computers in over 150 countries, with losses estimated to be over $1 billion. As a result, many of the affected organizations were forced to pay the ransom or face huge financial losses.

WannaCry malware screenshot from an infected system
This attack highlighted the need for better detection and response measures around ransomware and other cyber-attacks. Fortunately, ML/AI-based systems are proving to be a powerful tool in the fight against cyber threats. By using machine learning algorithms to analyze data and detect patterns, security teams are able to detect and respond to ransomware and other cyber-attacks more quickly and effectively.
Machine learning techniques are applied in various ways for ransomware detection. Here are two examples showcasing the utilization of machine learning in ransomware detection:
Behavioral Analysis
Machine learning algorithms can analyze the behavior of software or processes to identify potential ransomware activity. By training models on a dataset of known ransomware behaviors, ML algorithms can learn to recognize patterns indicative of ransomware attacks. For instance, ML models can detect file encryption behavior, abnormal network communication patterns, or unauthorized access to critical files. These models can identify deviations from normal behavior and raise alerts for potential ransomware incidents. This approach enables proactive defense against ransomware, even for previously unseen variants.
Anomaly Detection
Machine learning models can be trained to detect anomalies in system behavior that might be indicative of ransomware activity. By learning patterns from normal system operations, ML algorithms can identify deviations that suggest the presence of ransomware. This can include abnormal file access patterns, unusual process behaviors, or unexpected network connections. Anomaly detection models can effectively identify ransomware attacks by leveraging the power of ML in detecting deviations from expected behavior, allowing for early detection and response.
These examples demonstrate how machine learning empowers ransomware detection by analyzing behavioral patterns and identifying anomalies. By leveraging ML algorithms, organizations can enhance their defenses against ransomware threats and respond promptly to mitigate the impact of attacks.
Tools for Malware & Ransomware Detection 🛠️
CrowdStrike Falcon: CrowdStrike Falcon is a comprehensive endpoint protection platform that uses ML models to analyze behavioral patterns, file characteristics, and network traffic to identify and prevent malicious activities.
Palo Alto Networks WildFire: Palo Alto Networks WildFire is a cloud-based threat analysis platform that utilizes machine learning to detect and prevent malware and ransomware. WildFire leverages large-scale ML models trained on vast datasets to provide accurate detection and prevention capabilities.
Cisco Advanced Malware Protection (AMP): Cisco AMP is a security solution that combines machine learning with threat intelligence to detect and prevent malware and ransomware attacks. It uses ML algorithms to analyze file behaviors, identify malicious patterns, and make real-time decisions to block threats.
Sophos Intercept X: Sophos Intercept X is an endpoint protection solution that utilizes ML models to analyze file characteristics, behavior, and network connections to identify and block threats. Intercept X’s ML algorithms help detect and prevent both known and unknown threats effectively.
Symantec Endpoint Protection: Symantec Endpoint Protection leverages behavioral analysis and anomaly detection techniques to identify malicious behaviors associated with ransomware attacks. Symantec Endpoint Protection can proactively detect and mitigate ransomware incidents.
McAfee Advanced Threat Defense (ATD): McAfee ATD is a security solution that utilizes machine learning and sandboxing techniques to detect and analyze ransomware threats. It uses behavior-based analysis to identify suspicious activities and employs ML algorithms to classify and respond to ransomware behavior.
Others: Trend Micro Deep Security, CylancePROTECT, FortiClient, Kaspersky Endpoint Security, etc.
Challenges and Limitations 🤖
Using machine learning and artificial intelligence for malware and ransomware detection has many benefits, but there are some important challenges and limitations to consider.
Low-Diversity Training Data Sets
The success of any AI-based system often depends on the training dataset used to power it. If the dataset is too small or not diverse enough, the system may not be able to detect more sophisticated types of malware or ransomware.
False Positives and Negatives
A common issue with ML/AI systems is the risk of false positives (identifying benign activities as malicious) and false negatives (not detecting malicious activities). These errors can have serious consequences, leading to potential impacts on user productivity and security.
Privacy Concerns
Many AI-based solutions rely on collecting large amounts of personal data in order to detect subtle patterns that would otherwise be missed. This can lead to significant privacy concerns, as users may not be aware of or comfortable with their data being processed in this way.
While ML and AI show great promise, there are several challenges that need to be addressed. Adversarial attacks, where attackers manipulate ML models, pose a significant threat. Researchers are actively exploring defenses against these attacks (Kurakin et al., 2018). Handling imbalanced datasets, scalability, and interpretability are other areas of concern, requiring further research and innovation.
Future Directions and Emerging Trends 🚀
The future of ML and AI in malware and ransomware detection is exciting and promising. Deep learning, particularly convolutional neural networks (CNN) and recurrent neural networks (RNN), hold potential for improved accuracy and feature representation. Privacy-preserving techniques like federated learning enable collaboration among organizations without compromising data privacy.
One direction is the development of explainable AI models, where efforts are made to make ML algorithms more transparent and interpretable, enabling better understanding and trust in their decision-making processes. Additionally, there is an increasing emphasis on adversarial machine learning, which aims to detect and defend against attacks that attempt to manipulate ML models. Another trend is the integration of machine learning with other technologies like threat intelligence, big data analytics, and cloud-based security platforms to improve the efficiency and accuracy of malware and ransomware detection. As the threat landscape evolves, the use of machine learning will continue to play a critical role in strengthening cybersecurity measures, enabling faster and more proactive defense against emerging and sophisticated threats.
Conclusion 📝
In conclusion, the use of machine learning and artificial intelligence for detecting and thwarting malware and ransomware threats has the potential to revolutionize the world of cybersecurity. As the cybersecurity landscape grows increasingly complex, ML and AI provide a powerful arsenal to combat the ever-evolving threats of malware and ransomware. By leveraging these technologies, we can develop more robust detection and mitigation strategies. While challenges remain, ongoing research and collaboration between industry and academia will continue to drive innovation, enabling a safer digital environment.
As the technology continues to evolve, it is critical to stay abreast of the latest developments in this field. By understanding the challenges and opportunities posed by the use of ML/AI, organizations can gain a better understanding of the cybersecurity risks they face in order to better prepare and protect themselves. As the research continues to be conducted and we gain a greater understanding of the potential threats, the use of ML/AI in the realm of cybersecurity will open up new and exciting possibilities for the future.
References
[2] Intelligent Security: Using Machine Learning to Help Detect Advanced Cyber Attacks https://info.microsoft.com/rs/157-GQE-382/images/EN-GB-CNTNT-WhitePaper-Microsoft-Security-GEP-MECH.pdf
[3] Zahra Moti, Sattar Hashemi, Hadis Karimipour, Ali Dehghantanha, Amir Namavar Jahromi, Lida Abdi, Fatemeh Alavi (2021). Generative adversarial network to detect unseen Internet of Things malware, Ad Hoc Networks, Volume 122, 2021, 102591, ISSN 1570-8705, https://doi.org/10.1016/j.adhoc.2021.102591
[4]
Kolosnjaji, B., Zarras, A., Webster, G., Eckert, C., & Kruegel, C. (2018). Deep learning for classification of malware system-call sequences. Proceedings of the 2018 ACM SIGSAC Conference on Computer and Communications Security, 241-257.
This research paper explores the use of deep learning techniques for classifying malware based on system-call sequences. It delves into the methodology of employing recurrent neural networks (RNNs) to capture sequential dependencies in system-call traces, achieving high accuracy in malware classification.
Saxe, J., & Berlin, K. (2015). Deep neural network based malware detection using two dimensional binary program features. International Conference on Machine Learning and Applications, 369-374.
The paper by Saxe and Berlin introduces a deep neural network (DNN) approach for malware detection. It focuses on utilizing two-dimensional binary program features to train DNN models, effectively capturing the structural characteristics of malware. The study demonstrates the effectiveness of their proposed methodology in accurately detecting malware samples.
These research papers provide detailed methodologies, techniques, and experimental results for using machine learning in the context of malware detection.